In 2023, the average worldwide cost for each data breach was $4.45 million.
That means companies had to pay/lose an average of $4.45 million when faced with a data breach after not following security best practices for software development.
That’s a huge figure. Not something that most companies out there can afford. Also, several of these companies succumbed to financial failure after facing security breaches. The fines, lawsuits, customer backlash, and monetary loss related to software security breaches can really derail a business.
This makes security an important consideration for software development. In this blog, we will walk you through the top 10 secure software development best practices that can help you avoid disastrous outcomes.
Why is security best practices for software development often skipped?
Would someone forget to lock their safe? That’s highly unlikely, right?
So then why do software developers and businesses forget about software development security best practices?
Well, there can be many reasons for that. Some of the common reasons include:
- Not fully understanding the importance of security best practices for software development.
“We’re a small startup; security can wait until we have a larger user base and more resources to dedicate to it.” - More focus on creating features quickly rather than making sure those features are secure.
“Our competitors are moving fast. We need to prioritize getting our product to market quickly and can deal with security concerns later.” - Lack of awareness about potential risks and the potential damage that security breaches can cause.
“Our software isn’t dealing with sensitive information anyway. Even if there’s a breach, it wouldn’t cause significant harm.” - Assuming that following secure software development best practices is someone else’s responsibility, not theirs.
“Isn’t security the job of the cybersecurity team? They’re the experts; we should focus on our core responsibilities in development.” - Higher cost of software development if software development security best practices are followed:
“Implementing software development security best practices will significantly increase our development budget. We can’t afford to allocate resources to security when we’re trying to keep costs down.”
No matter what the reason is, it is important for you to understand that you cannot skip on security best practices for software development.
At SynergyTop, we have designed and developed 500+ websites, web applications, mobile apps, digital products, and software solutions. Never once have we faltered on security in any of these projects.
Our continued commitment to secure software development is what has saved our clients from any security breaches and legal consequences thereof.
Below, we are mentioning the top software development security best practices that we follow.
Read on.
Software Development Security Best Practices
1. Follow Secure Coding Standards
Security coding standards are established rules and guidelines to be used while writing software code to minimize security risks. Some examples of secure coding guidelines include OWASP Top 10 or SANS Top 25.
Important: Software developers should stay updated with these coding guidelines as these get revised from time to time. See the updated OWASP Top 10 guidelines for 2021 below:
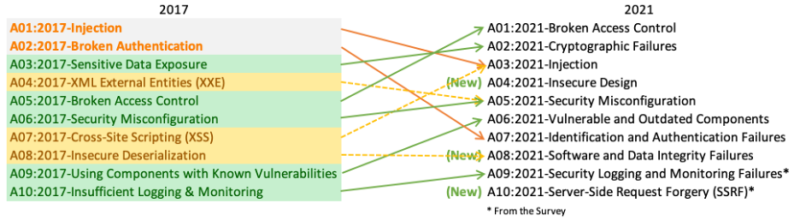
Secure development practices ensure that developers write code that’s less prone to being exploited by attackers or malicious software.
For instance, one secure coding standard is to always validate and sanitize input from users. This means checking the information users input into the software and making sure it’s safe to use.
2. Regular Security Testing
Security is not a one-time activity. You cannot follow a few software security practices and hope to keep your system safe always. Regular security testing is important to identify weaknesses in the software and fix them before they are exploited.
Software security testing involves conducting assessments and evaluations of software systems. Techniques like penetration testing, vulnerability scanning, and code reviews are used for this.
It is also important to integrate automated security testing tools into the development pipelines to detect vulnerabilities early in the software development lifecycle.
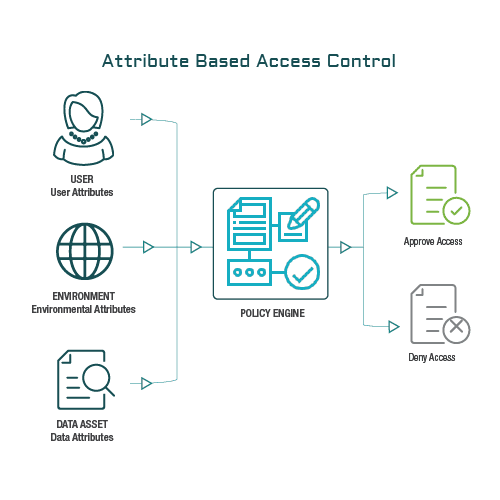
3. Implement Access Controls
Imagine what would happen if you let everyone in your office access important documents or the safe. That would be a major security vulnerability, right?
Well, the same is true for secure software development. You cannot let everyone access everything in your software. Access controls act like digital gatekeepers that decide who gets to see or change certain things in your software application.
The principle of “least privilege” is followed in this regard, which means people only get access to what they absolutely need.
To set up access controls, software developers must first decide who should be able to do what, and then make rules accordingly. There are two main types of access controls:
- Role-based access control (RBAC): Access permissions are assigned based on predefined roles such as “admin,” “user,” or “manager.”
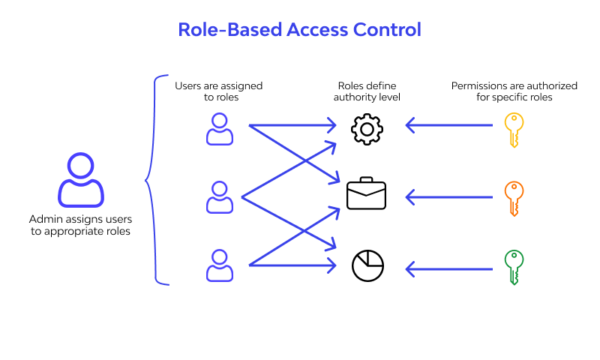
- Attribute-based access control (ABAC): Access permissions are determined by specific attributes of the user, resource, or environment, like user location, time of day, or security clearance.
4. Patch Management
When a software solution is developed, bugs and vulnerabilities can be identified later on. When that happens, organizations release patches to fix the identified security vulnerabilities.
Patch management is the systematic process of identifying, acquiring, testing, and applying patches to software systems.
Let’s say you’re managing a web server using Apache software. You receive a notice about a serious security flaw in Apache that could let attackers take control of your server. To fix it, you download and test the patch provided by Apache. Once you’re sure it works, you apply it to your server during a maintenance window. You then keep an eye on the server to make sure the patch doesn’t cause any problems.
To streamline the patch management process and ensure timely updates, you can also leverage automation tools and systems. Automation helps reduce the risk of human error and ensures that critical vulnerabilities are addressed promptly.
5. Data Encryption
Data encryption involves encoding data in such a way that only authorized parties can access it.
It helps protect sensitive information from unauthorized access or interception. To implement data encryption, developers should use strong encryption algorithms such as AES (Advanced Encryption Standard) and TLS (Transport Layer Security) for data in transit.
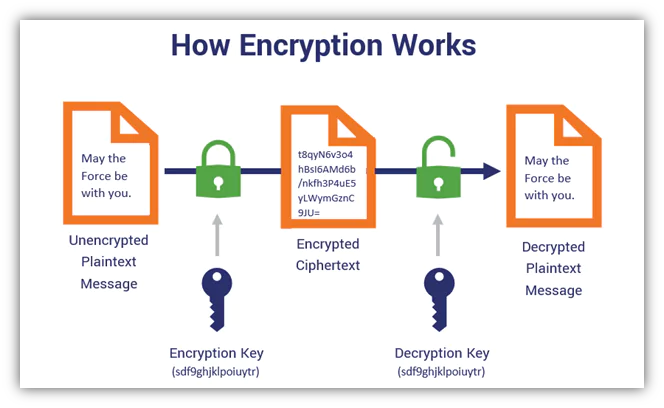
They should also encrypt sensitive data stored in databases or files using encryption libraries and tools provided by their programming languages or frameworks.
6. Monitoring and Logging
Monitoring and logging involve continuously monitoring software systems for security events and logging relevant information for analysis and investigation. This helps detect security incidents in real time and provides valuable insights into system activity.
To implement monitoring and logging, software developers instrument their applications to capture security-relevant events and logs. Centralized logging solutions and security information and event management (SIEM) systems are used to aggregate and analyze log data effectively.
7. User Authentication
Authentication is the process of verifying the identity of users trying to access a system. It ensures that only legitimate users are able to access the information.
Passwords are the simplest form of authentication used by software developers. You can access your account only with the right password. Other methods of authentication include multi-factor authentication (MFA).
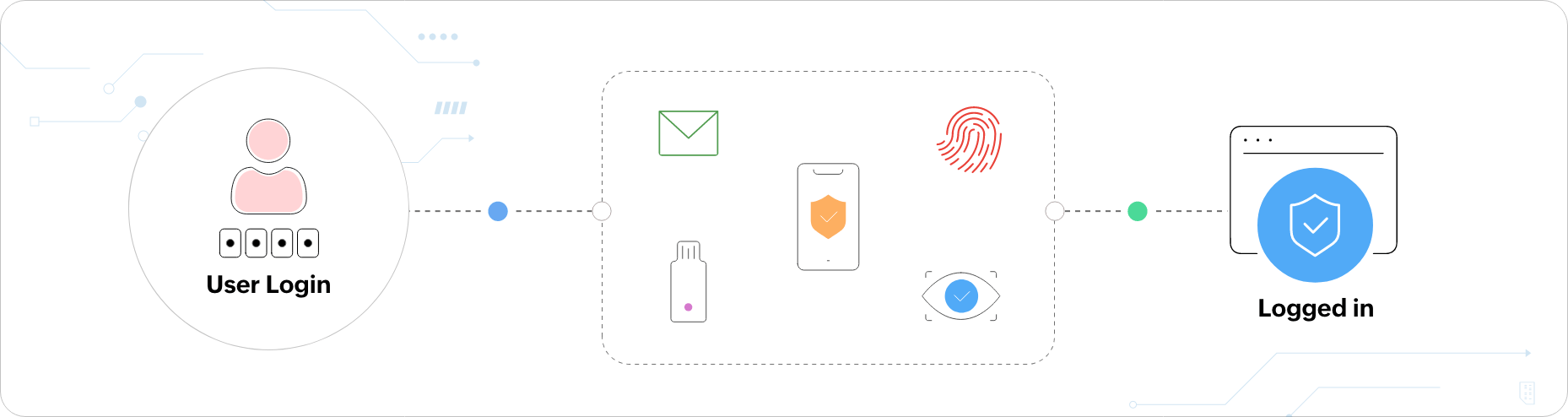
This adds an extra layer of verification, like sending a code to a user’s phone after they’ve entered their password, to enhance security. Biometric authentication, like fingerprint or facial recognition, uses unique physical traits to confirm identity.
Important: Best Practices for Secure Software Development Throughout The Lifecycle
Security has to be a key area of focus throughout the software development lifecycle (SDLC).
best practices for secure software development, thus need to be incorporated into the process right from the initial design phase throughout the development process.
Further, it is also important that software development companies extend security training and awareness to all members of the team. This fosters a security-conscious culture within the organization and empowers individuals to recognize and address security threats effectively.
Getting Started With Secure Software Development Best Practices
While that’s a wrap on the top 10 best practices for secure software development, the list by no means is exhaustive. There are several other security best practices for software development that need to be followed to ensure safety.
The best way to ensure that you don’t miss out on the best practices for secure software development is to work with software development teams that keep security as their priority. A reliable software development company will not just help you keep your software secure but also make sure you are adequately prepared to tackle any security vulnerabilities.
FAQs
Worried about your software’s security? Schedule a consultation to get a comprehensive security audit for your software today!